A shell is a text-based command line that allows you to control your computer remotely. It is a replacement for programs like telnet, which transmit your username and password in plain text, making them vulnerable to snooping by a malicious third party.
Programs that let you securely connect to remote computers over an encrypted connection are called SSH clients. Often these come with a tabbed interface that lets you easily switch between different remote sessions.
Secure Shell
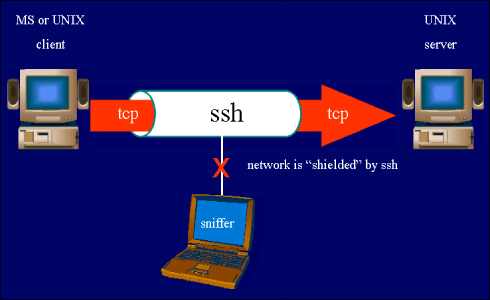
Secure Shell uses public-key cryptography to provide strong verification and encrypted communication between a client and server. It allows system administrators to remotely log in and manage a server, transfer files and tunnel other traffic. VanDyke Software provides mature native Windows SSH clients and servers that can meet the demands of most enterprise environments, sneak a peek at this website.
When you connect to a remote server via SSH, an authentication prompt appears on the host computer. Enter your passphrase and account password to confirm your identity, then conduct transactions on the remote server. Your password and commands are encrypted during transmission.
If you connect to a remote host more than once, the host might ask you to accept its public key. When you reply, the host’s key is stored in the known_hosts file on your local system. This information can be used to gain authenticated access to your local system even after the host is removed from service or your account is terminated.
Tunneling
The SSH protocol suite allows you to tunnel other network traffic through an encrypted connection. This can be helpful for working around restrictive firewall settings or encrypting otherwise unencrypted data.
For example, suppose a server administrator needs to make changes on a server inside a private network. The server only accepts data packets from other servers within the same private network, but the administrator wants to connect to the server from outside the private network. The administrator could use SSH tunneling to forward data packets from a local computer, whose ports are not vulnerable to attack, to the server.
In order for this to work, the local port and hostname of the client must match those of the server. This is done using the -L command-line option, which specifies that the local port of the client should be forwarded to the remote host and port. By default, the local system stores this information in a hidden file called /.ssh/known_hosts in the user’s home directory.
File Transfer
Unlike common programs like telnet, SSH doesn’t transmit your username and password in plain text. This means that any malicious third party who snoops on your network traffic will only see a bunch of random characters and will be unable to decipher your password.
Instead, SSH uses a private key to authenticate with the server, creating a secure data channel while keeping the command channel open for communication. This makes it possible to transfer files between servers, as well as perform remote commands on a host computer.
Many SSH client programs have features to automate and simplify file transfers, remote command execution, port forwarding, and other tasks. For example, Bitvise’s SSH client includes sexec, a scriptable command-line program that executes remote commands from batch files. The output from a remote program can then be captured and processed. SSH is used by system administrators for remote logins to servers, switches, routers, and virtualization platforms to manage operating systems, test applications, backup databases, change passwords, and manage user access.
Remote Administration
Remote administration is the process of controlling a computer remotely. This can be done from any location that has internet access. This allows users to manage a site as though they were physically sitting in front of the machine. This can be done using various software packages, such as Windows’ built-in Remote Desktop Connection or free cross-platform alternatives such as VNC.
The SSH protocol provides a secure way to perform remote administration. Older remote management protocols, like Telnet, transmitted administrators’ commands in a form that anyone could see (think of it like an employee putting the store owner on speakerphone when they give instructions). SSH is more secure, and encrypts the commands that are sent between client and server.
Summary:
SSH can also be used to authenticate with a remote server without a password. This is accomplished by generating a public/private key pair on the client, and distributing the public key to servers where it is needed.


